Azure RBAC roles are a key component of Azure Security because it restricts who can perform what actions on your Azure resources. It also helps you to implement an appropriate level of control for the right user, group, or application accessing your data. In this blog, we will learn about Azure Role-based access control roles. The security of Azure resources is always a crucial aspect of any Azure administrator’s role. As an administrator, if you need to protect your data and assets while providing access to employees and partners as required, the Azure RBAC role is a good fit for you.
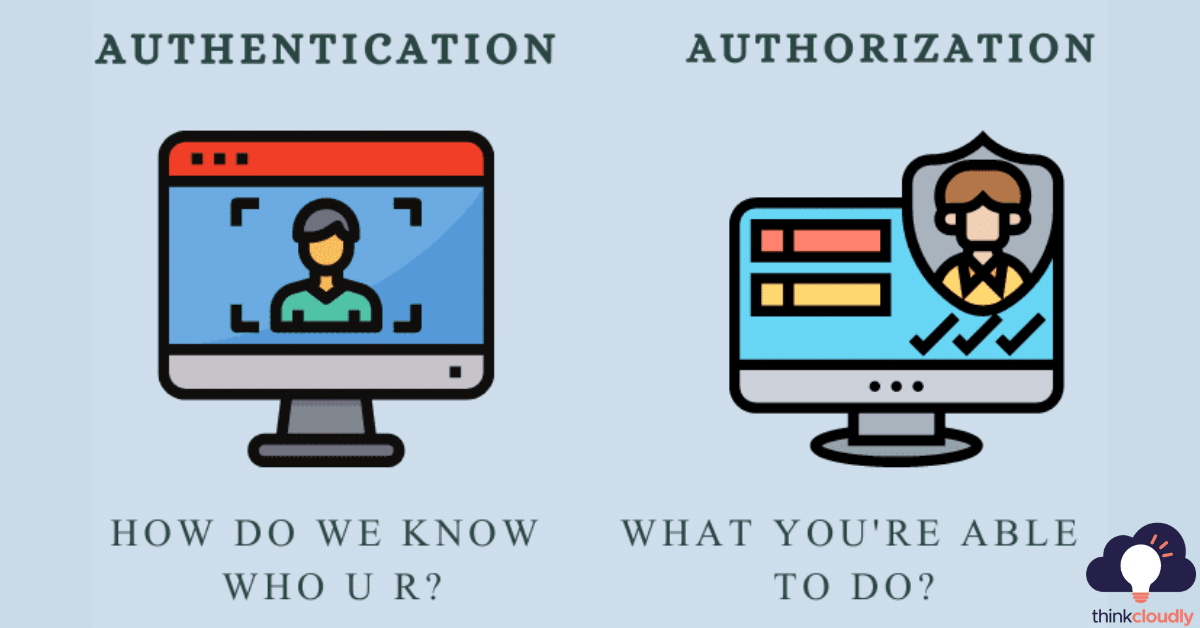
Authentication vs Authorization
Authentication is a way for individuals and things to prove who they are. From small children with their birth certificates to security cameras at the office building’s entrances or public transportation riders’ smartphones – authenticating has become an integral part of our lives!
It can also be referred to as identification and confirmation, but in this case, only one word means what you might think it does–that’s why people often refer back and forth between these two usages!
There are three methods by which an information provider may authenticate its client: through Something You Know (i.e., password), something they have (a special device such as a token) -or even their behavior patterns, Basically meaning “how do we know who u r?”
Authorization in system security is the process of giving users permission to perform certain actions, like accessing a resource or function on your computer. This term often gets used interchangeably with client privilege which refers specifically to how much access an individual has within their own session (i.e., what you’re able to do).
What are Azure RBAC roles?
Azure RBAC role is an authorization system in Azure that helps you manage who has access to Azure resources, what they can do with those resources, and where they have access.
User roles allow us to categorize users and define what permissions they have on different account assets, such as what data those users can read or modify.
Role-based access control (RBAC roles) allows you to assign different permissions for various services in the cloud. This includes databases, app services, and even virtual machines! The authentication process is handled by Azure Active Directory while authorization remains at a role level rather than an individual object such as database users or computer accounts.
Incorporating Azure RBAC best practices is crucial for robust security management within your Azure environment. When implementing Azure Role-Based Access Control (RBAC), it’s essential to adhere to established guidelines and principles to ensure a secure resource access framework. One such best practice involves the careful utilization of Azure’s predefined roles, such as the ‘Security Reader’ role, which grants users read-only access to security-related data without compromising sensitive configurations. By assigning the ‘Security Reader’ role judiciously, you can strike a balance between granting necessary access for monitoring and auditing purposes while safeguarding your Azure resources from unauthorized changes or vulnerabilities, ultimately enhancing your overall Azure security posture.
What does this mean? It ensures that each user has only those roles they are assigned so there’s no possibility of unauthorized activity happening on your network because somebody else got lucky with guessing their password – it’s always known who these people really belong to thanks to reliable secure systems like multi-factor auth where other factors besides passwords play important parts when authenticating yourself against third-party applications.
Build Your Career as a
Azure Cloud Architect
- Live Projects
- Resume / Interview Preparation

The RBAC system has three primary rules:
- Assignment of Role: A user is only able to make use of permission if he has been assigned a role.
- Role authorization: A user’s active role must authorize for the user. Combined with rule 1, this rule ensures that only authorized users can take on particular parts.
- Permission authorization: A user cannot exercise permission if the permission does authorize for his active role. By combining rules 1 and 2, this rule ensures that users no longer have access to licenses other than those they have given.
Concepts:
Assigning roles involves defining a role, defining its scope, and defining the security principle.
Security Principal – an object that represents a user, group, service principal, and managed identity for Azure.
Role Definition – the set of permissions that can be carried out, for instance, reading, writing, and deleting.
Scope – A collection of resources that have access.
Best practices
- Using Azure RBAC, you can segregate team members’ responsibilities and only grant access to those who need it.
- Reduce the possibility of a compromised owner breaching the system by limiting the number of owners (maximum 3).
- Using Azure AD PIM, users can protect privileged accounts from malicious attacks.
Boost your earning potential with Azure expertise. Explore our certified Azure Courses for a high-paying career
- Explore Azure DevOps Certification
In this lab, we will assign the RBAC role to the resource group.
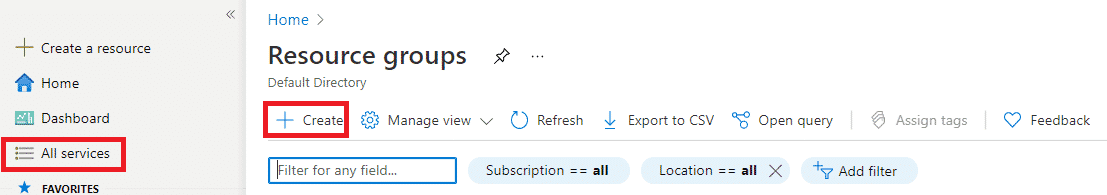
- Login to Azure portal
- In All services, search for Resource group and click on it.
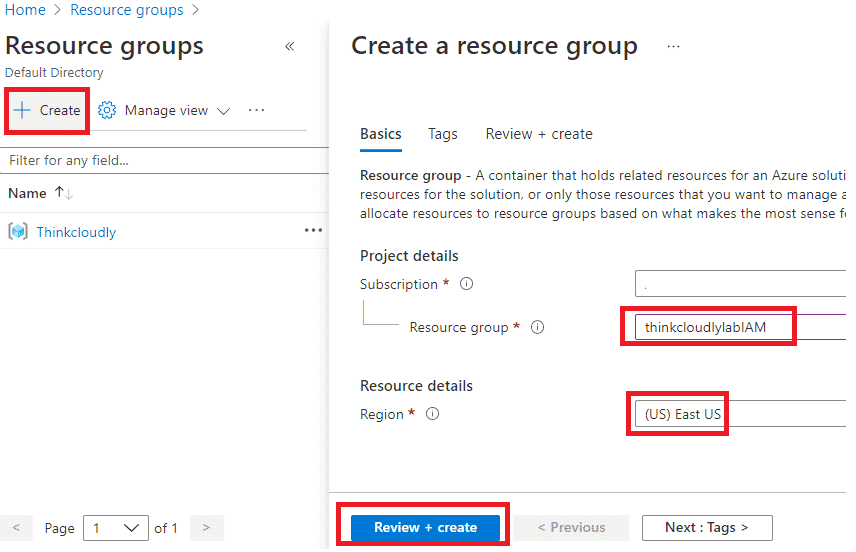
- In the Resource group blade, click on +Create and give the Name of resource group as thinkcloudlylabIAM and Select region as (US) East US and click on Review + Create. After validation, click on Click
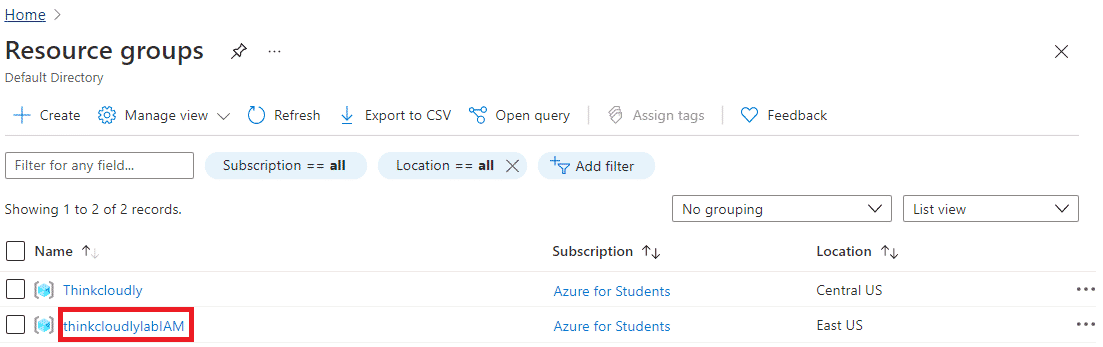
- You may access the newly created resource group by refreshing the page and clicking the entry.
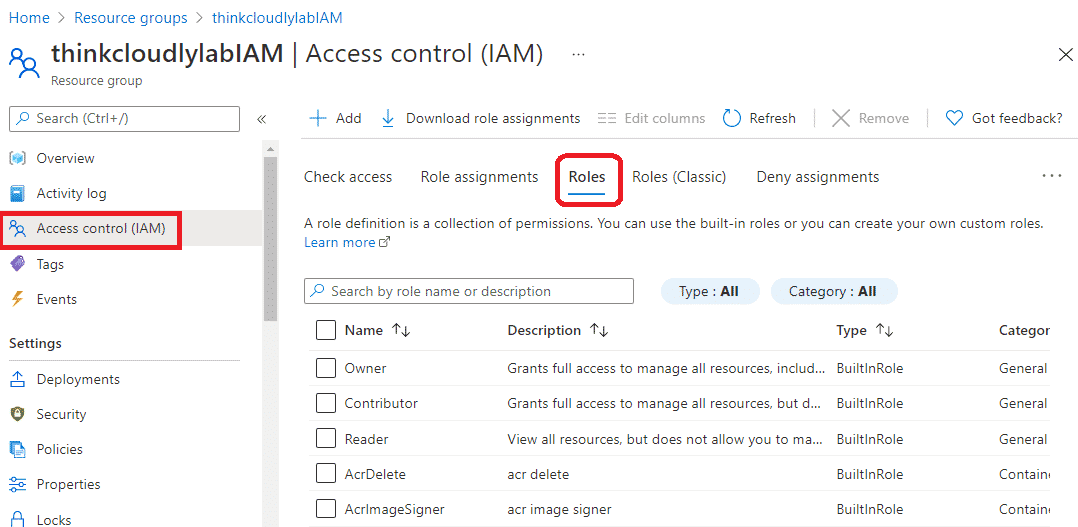
- On thinkcloudlylabIAM blade, please click on the IAM tab on the left-hand side and click on Roles.
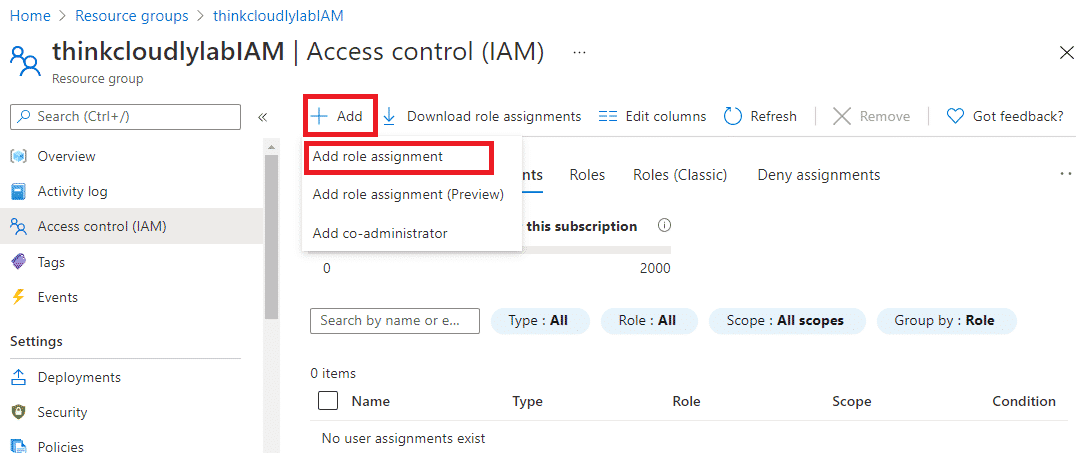
- Now, click on Role Assignments and click on +Add and then click on Add role assignment.
There are more than 140 roles built into Azure. Four fundamental roles are built-in, however:
Owner: Owners have full access to the scope and can delegate access to others
Contributor Has the same privileges as an Owner but cannot delegate access to others.
Reader: View Azure resources
User Access Administrator: Lets you manage user resources and access them.
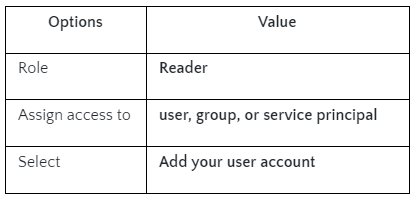
- Fill in the details on Add Role Assignment as per the below table:
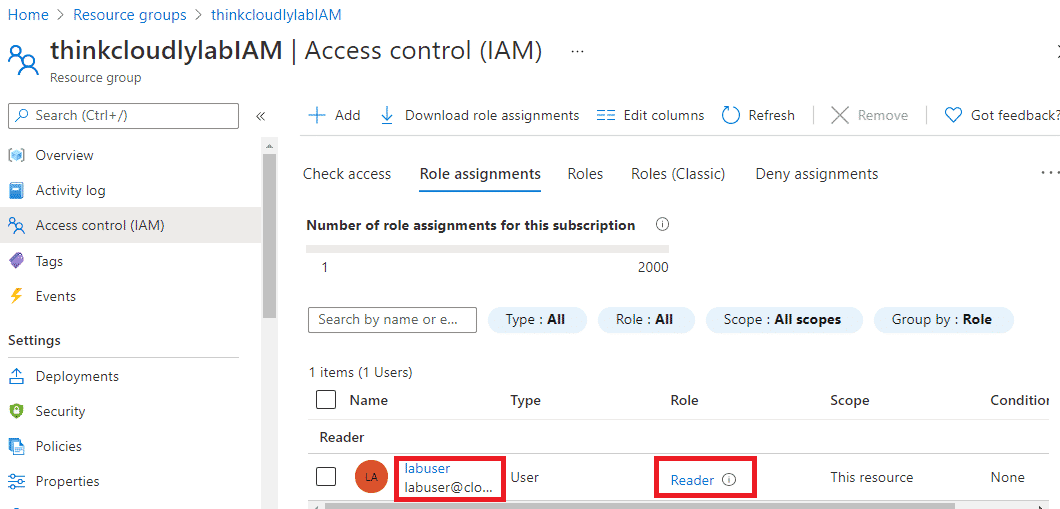
- Now on the IAM page, you will be able to see the newly created READER role. If you are unable to see that, please refresh the page.
Congratulations!! You have created an Azure RBAC role and assigned it to a user.
Managing RBAC roles using PowerShell
Now try adding and managing Azure RBAC roles using PowerShell, for that please configure PowerShell and then use the below commands:
Get-AzSubscription
$subScope = "/subscriptions/00000000-0000-0000-0000-000000000000"
New-AzRoleAssignment -SignInName testuser@something.com -RoleDefinitionName "Reader" -Scope $subScope
Get-AzRoleAssignment -SignInName testuser@something.com -Scope $subScope
Thanks for reading. I hope you enjoyed it. Our team will continue to provide ways to leverage Azure concepts!
“Azure Security Reader Role: RBAC Insights”
“Azure RBAC (Role-Based Access Control) empowers you to manage access to Azure resources effectively. Within this framework, the ‘Azure Security Reader’ role plays a vital role. This role specializes in providing read-only access to security-related information across your Azure environment. By assigning the ‘Azure Security Reader’ role to users or groups, you grant them the specific permissions needed to view security configurations, monitor compliance, and gain insights into security-related data. This tailored access ensures that individuals have the necessary visibility without compromising other operational aspects. Utilizing the Azure Security Reader role as part of your RBAC strategy enhances your security posture by promoting the principle of least privilege while facilitating the monitoring and analysis of security settings.”
Azure is really interesting to study. Experience conceptual and practical knowledge with Thinkcloudly. Explore our more free resources on Azure:
- Practice with Azure live project training.
- Read the blog over Azure live projects.
- Read Azure networking interview questions
- Read top Azure interview questions and answers.
- Don’t forget to register for our free webinars on Azure.
Conclusion:
Access management is an essential part of cloud governance, which should be given the highest priority. In order to ensure that the organization adheres to the industrial standards of data security, it helps define a set of rules for utilizing and controlling cloud resources. A secure Azure environment and independent security principles can be achieved by implementing RBAC at the right level.














No comment yet, add your voice below!